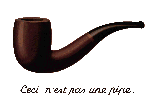
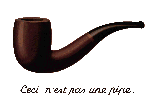 |
Frequently Asked Questions about The Coroner's Toolkit |
What systems does it run under?
Why isn't it GPL'd? What license is it under? Is it free?
Can I put it on a CD in a book, Unix distro, etc.?
How can I get in touch with Wietse or dan?
I heard that they did a class on this stuff - when will they do it again?
I've just been broken into. Help!
I've just deleted a file. Help!
Is there a mailing list that discusses the TCT?
What's the deal with that little pipe?
I have a large file (greater than 2 GB) that lazarus says it can't open. What can I do?
Where do I get it? TCT is available in two main locations:
http://www.fish.com/tctand
http://www.porcupine.org/forensics
What systems does it run under?
Currently the following OS's are at least semi-supported (e.g. the more
recent versions of the OS should work):
FreeBSD 2-4.*
OpenBSD 2.*
BSD/OS 2-3.*
SunOS 4-5.*
Linux 2.*
Why isn't it GPL'd? What license is it under? Is it free? The TCT is essentially free for most purposes. While we applaud the GPL and what it has done, we're not personally interested in using it. Wietse, working for IBM, has to release his work under IBM's Public License Version 1.0. dan has released pretty much all his stuff by a very slightly modified BSD version. The work is therefore somewhere between the two; files that are explicitly authored (in the code or documents) to be authored by Wietse are covered by the IBM's license, the rest are either by the modified BSD or some combination of the two. A bit of a mess, we're not anticipating any legal challenges. Ask us if you have any doubts or questions.
Can I put it on a CD in a book, Unix distro,
etc.?
You're welcome to redistribute it as long as (a) give us credit for
our work, (b) keep it intact, and (c) follow what our copyrights/license
statements say. We'd also appreciate being notified, but that's not
a requirement.
How can I get in touch with Wietse or dan? E-mail to both authors can be sent to tct@fish.com. We'll try to answer it, but please be aware that we only work on TCT in our (very) part time. You might also try posting to comp.security.unix for answers. Failing either of these, you can send mail directly to dan or Wietse:
zen@fish.com
wietse@porcupine.org
I heard that they did a class on this stuff - when will they do it again? While we did do a class on forensic computing (the notes are online), we will probably not do it again, as it was mostly a vehicle we utilized to teach ourselves more about the material you see before you.
I've just been broken into. Help! First of all, we do not have the time or resources to personally help you with your investigative problems. And since there's no way we can think of telling you in a way that will soften the blow, let us simply say it outright - WRT the TCT, you're probably out of luck. The tools probably won't help you out unless you've already looked at it, played with it, and know what the tools do as well as what to expect from them. The investigation of breakins can be a very complex subject.
That said, they still might help and you may get lucky. Don't give up! Download them on a clean, undamaged system and read the documentation. There's a short tutorial we put together that might assist you. Good luck!
I've just deleted a file. Help! Unix is rather unforgiving when you blow away files. However, the unrm and lazarus tools (in TCT) could help, and there's yet another short tutorial we put together that might assist you getting your data back. Good luck!
Note - if you're running Linux there are a couple of other resources you might investigate -
A document on how to recover deleted files
Is there a mailing list that discusses the TCT? Yes, there is a mailing list (with on-line archive) for sharing experiences. To subscribe, send a message to majordomo@porcupine.org with body (not subject): subscribe tct-users. The list will reject mail from non-members so it is unlikely to catch UCE. To unsubscribe, send mail with as body (not subject): unsubscribe tct-users.
I'm interested in learning more about forensic computing, etc. Can you suggest any good reading material? Check out the bibliography we include in the toolkit.
What's the deal with that little pipe? The image is taken from René Magritte's 1929 painting "La trahison des images", which is usually translated as "The Treachery of Images" or "The Betrayal of Images". The image is of a pipe with writing underneath, which says "Ceci n'est pas une pipe" - or, "This is not a pipe." Magritte, when asked why the image he had painted was not a pipe, reportedly responded "because I can't use it as a pipe".
At first blush this might seem to be a trivial or even foolish statement, but this would be a serious mistake to make.
We use this as our primary metaphor for our work in forensic computing analysis. What we're examining is never the actual object - it is always a representation, usually several layers and abstractions removed - of the actual thing, which we can never truly ascertain. The image could be an artist's rendering of a real pipe. It could also be completely made up by the artist. It could be a seriously flawed copy of the real item. You can't tell the difference simply by looking at the image.
Computers are subject to the treachery of images as well. The image on your computer screen is not a computer file - it's only an image on a computer screen. Images of files, processes and network connections are very distant cousins of the actual bits in memory, in network packets, or on disks. The images that you see are produced by layer upon layer of hardware and software. When an intruder compromises a system any of those layers could be tampered with. Application software can lie, operating system kernels can lie, boot PROMs can lie, even hard disk drives can lie.
We feel that all these complexities are superbly displayed by M. Magritte, who illustrates in this and other works how the appreciation and understanding of concepts and objects exist on many different levels.
I have a large file (greater than 2 GB) that lazarus says it can't open. What can I do? Lazurus uses perl to process the file. In order to access large files you need to use an operating system and perl binary that can handle such a large file (such as *BSD systems, Solaris with a perl compiled under 64 bit support, and Linux systems with kernels and a version of perl that is compiled for large file support.)